BlackSuit Ransomware exploit over Fake Zoom calls >>>
In a meticulously orchestrated cyberattack, a threat actor leveraged a malicious Zoom download to infiltrate a corporate environment, patiently dwelling for nine days before deploying BlackSuit ransomware across the network. The case, analyzed by The DFIR Report, provides a textbook example of how attackers blend stealth, social engineering, and layered toolkits to gain maximum control before unleashing devastating payloads.
“This case from May 2024 started with a malicious download from a website mimicking the teleconferencing application Zoom,” the report explains.
It began on a fake Zoom site, zoommanager[.]com, which presented a cloned interface nearly indistinguishable from the real thing. When the victim clicked the “Download” button, they unknowingly triggered a chain reaction—a weaponized installer crafted with Inno Setup, hiding the d3f@ckloader, a Pascal-based loader known for its use in Malware-as-a-Service (MaaS) operations.
The loader executed scripts to:Hide its files from viewExclude itself from Windows DefenderFetch second-stage malware from a Steam Community profile, using it as a makeshift C2 relayOne of the downloads was a legitimate Zoom installer, cleverly used to mask the malicious activity and lower user suspicion. But the second payload was the real danger—IDAT loader, used to inject SectopRAT into the MSBuild.exe process.
For over a week, SectopRAT silently maintained access, beaconing to Pastebin for its command-and-control configuration while performing no noticeable actions.
“After this, command and control traffic was established and activity ceased for eight days,” according to DFIR analysts. But on day nine, the attack escalated.
The intruders deployed Brute Ratel—a red team framework often used by advanced threat actors. One Badger DLL executed reconnaissance, while another (never used) hinted at a backup C2 path via the Tyk API gateway, showing operational sophistication.
This stage also marked the use of Cobalt Strike, with beacons injected into dllhost.exe. These beacons accessed LSASS memory for credential dumping, while lateral movement was executed via psexec_psh and RDP tunneled through a proxy called QDoor.
“The threat actor dropped a binary svhost.exe… a proxy tool known as QDoor,” enabling RDP tunneling through compromised domain controllers.
On compromised file servers, the actor downloaded WinRAR via Edge, compressed target directories, and exfiltrated nearly 1GB of data to Bublup, a cloud-based SaaS platform.
“The threat actor used WinRAR to archive various files and then upload them to a cloud SaaS application named Bublup.”
The use of legitimate tools like WinRAR and browsers further complicated detection efforts.
Having staged their payloads through temp.sh, the attackers executed a two-phase ransomware deployment using PsExec:
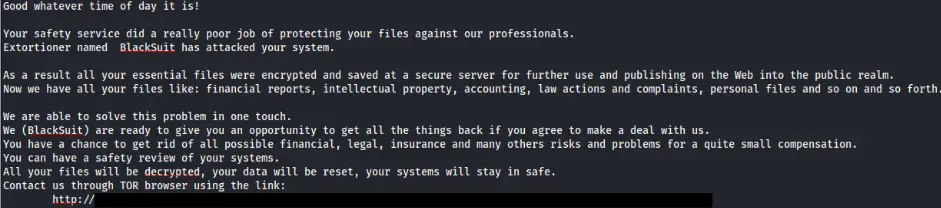
COPY.bat distributed the 123.exe ransomware to dozens of remote hostsEXE.bat initiated the encryption process across the enterprise“The ransomware was BlackSuit, which after execution… used vssadmin to delete shadow copies, encrypted local files, and then dropped a ransom note.”
The Time to Ransom (TTR): over 194 hours, or just over nine calendar days.