Mobile Devices exposed to IRS Attacks >>>
Cybersecurity experts have identified a sophisticated phishing campaign specifically targeting taxpayers through their mobile devices.
The attacks leverage the heightened anxiety of last-minute tax filers, creating a perfect storm for cybercriminals looking to harvest sensitive personal and financial information.
These attacks have nearly quadrupled since early February, with researchers noting a significant spike toward the end of the month as taxpayers rush to complete their filings.
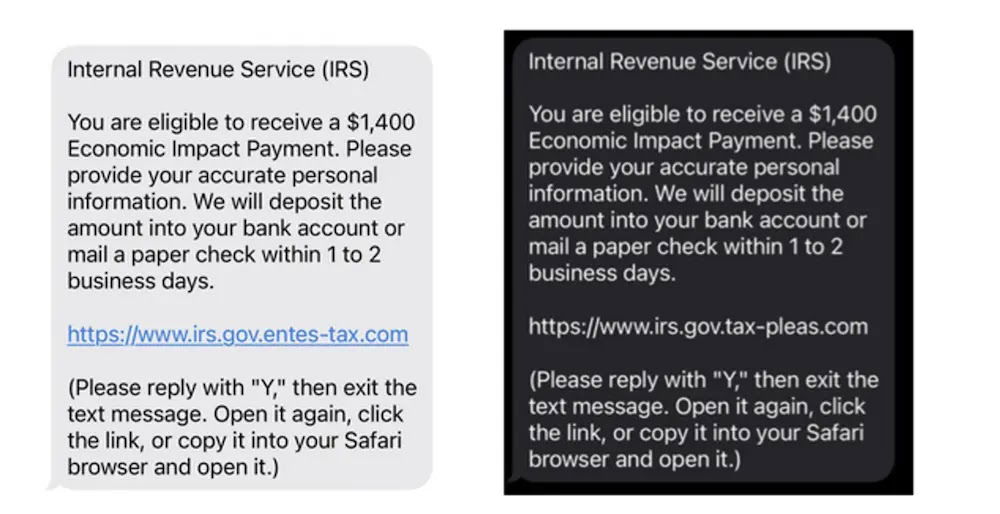
The campaign primarily utilizes SMS text messages as the initial attack vector, with scammers employing urgent language about tax refunds being on hold or threatening legal consequences for non-payment.
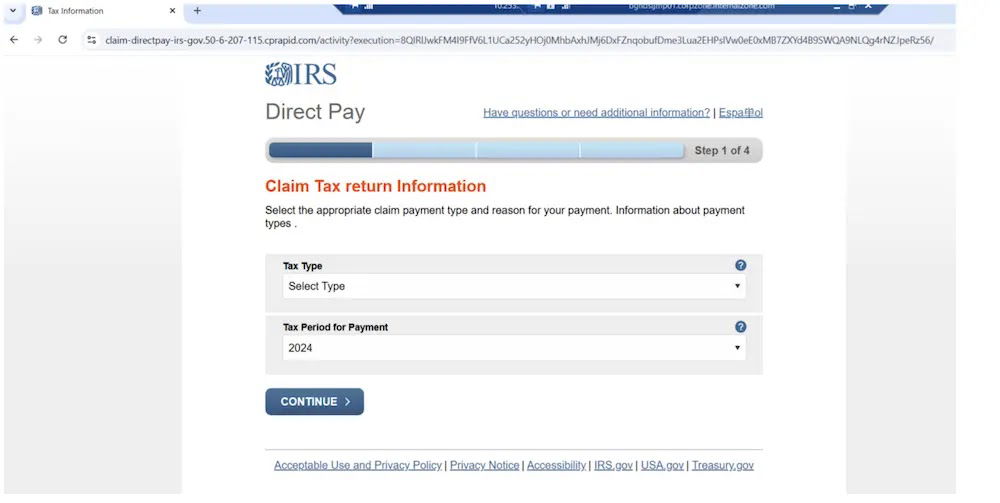
When recipients click the embedded links, they’re directed to convincing replicas of IRS websites specifically designed to capture personal information, including Social Security Numbers and financial details.
Nearly half of all taxpayers complete their returns between mid-March and April 15, creating a target-rich environment for these attacks.
McAfee researchers identified that these attacks employ sophisticated domain spoofing techniques, often weaving “irs.gov” into malicious URLs to create a false sense of legitimacy.
Examples include domains like “irs.gov.entes-tax[dot]com” and “irs.gov.tax-pleas[dot]com” that appear official at first glance but actually direct users to fraudulent websites controlled by attackers. Link shorteners are frequently employed to further obscure the destination of these malicious links.
Domain Spoofing Techniques --
The technical sophistication of these attacks lies in their ability to mimic legitimate IRS communications and web infrastructure.
When analyzing the attack infrastructure, security researchers found that the fraudulent sites employ advanced visual mimicry techniques to replicate the official IRS website.
These sites often incorporate official IRS logos, color schemes, and page layouts that make them nearly indistinguishable from legitimate government pages.
The attackers have developed a custom framework that dynamically adjusts to mobile device parameters, ensuring that the phishing pages render properly regardless of screen size or operating system.
The infection chain begins with the initial SMS message, which typically contains a shortened URL using common services like bit.ly or custom shorteners.
These links redirect through multiple hop points before landing on the final phishing page, making traditional URL filtering less effective.
The final landing pages use HTTPS certificates with names that include terms like “irs,” “tax,” or “refund” to further the illusion of legitimacy.
Once personal information is submitted, it’s immediately transmitted to command and control servers, often located in jurisdictions beyond the reach of U.S. law enforcement.
To protect themselves, taxpayers should verify all communications directly through the official IRS website and remain vigilant for the warning signs of these increasingly sophisticated attacks.