SVG Phishing Attack Flow Analysis >>>
In a world where images are meant to inform or entertain, a new breed of phishing attack is using them to deceive and steal. A recent report from Trustwave SpiderLabs reveals a 1,800% surge in phishing attacks using SVG (Scalable Vector Graphics) files as delivery vehicles. These lightweight, deceptively harmless image files are becoming a favorite tool of cybercriminals for credential theft, malware delivery, and multi-factor authentication bypass.
SVG files are used across the web for crisp icons and logos. Unlike PNG or JPEG formats, SVGs are XML-based and can embed JavaScript, allowing them to carry interactive code—or in this case, malicious scripts.
“Cybercriminals exploit this feature by inserting malicious scripts directly into SVG files… enabling unauthorized access, data theft, and identity compromise.”
SVG files are rendered natively by browsers, and most email clients don’t scan or sandbox them, making them ideal phishing vectors.
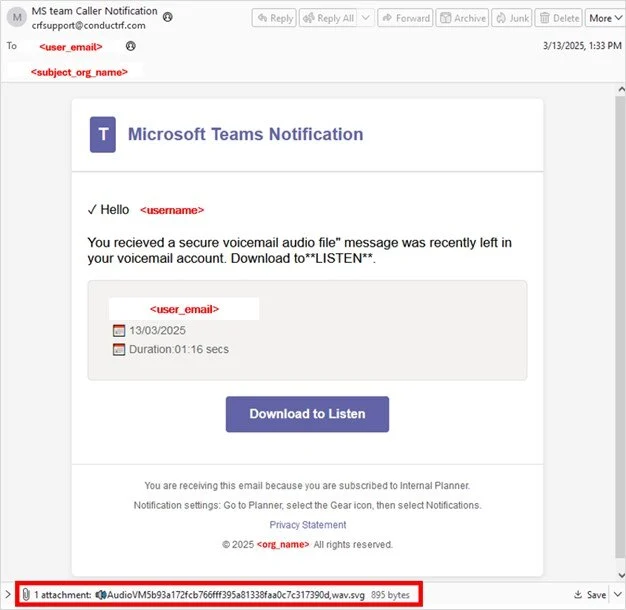
In one campaign, attackers mimicked a Microsoft Teams voicemail notification. The phishing email appeared legitimate and urged users to download a so-called audio attachment—a malicious .svg file.
“Despite its .svg extension, the file is crafted to appear like a voice message… When clicked, it executes embedded redirection code that leads users to a fake Office 365 login page.”
The script used the SVG <foreignObject> tag and base64 obfuscation, bypassing traditional email security tools. Once opened, the image rendered a fake Microsoft logo and redirected victims to a credential-harvesting page.
This campaign was linked to Mamba2FA, a Phishing-as-a-Service (PhaaS) group known for its ability to bypass MFA protections.
SVG-based phishing is now powered by sophisticated Phishing-as-a-Service platforms like:
Tycoon2FAMamba2FASneaky2FAThese kits enable attackers to:
Embed multi-layered obfuscated scripts into SVGsConduct Attack-in-the-Middle (AiTM) phishingRedirect users to pages that bypass MFA and harvest credentials“The rise in SVG phishing suggests that threat actors are continuously expanding their tactics to bypass security measures beyond QR codes and the traditional methods, including links, HTML, and document-based attacks,” the report concludes. To combat this threat, Trustwave SpiderLabs recommends a multi-faceted approach:
Consider blocking or flagging SVG attachments: Evaluate the option of blocking emails with SVG attachments or, at a minimum, flagging them with a warning.Be cautious with attachments and links: Treat unexpected files and embedded links with suspicion.Verify authenticity: Double-check senders and content.Train employees regularly: Provide ongoing education on phishing trends and techniques.Use advanced protection: Implement robust filtering and threat-detection systems.Implement MFA methods with extra layers: Strengthen defenses with phishing-resistant methods.