WordPress Plug-in Vulnerability CVE-2024-13496 >>>
A critical vulnerability in GamiPress, a popular WordPress plugin used for gamification and rewards systems on websites.
The high-impact flaw, categorized as CVE-2024-13496 with a CVSS 3.1 score of 7.5, allowed unauthenticated attackers to inject malicious SQL queries that could potentially compromise entire WordPress installations.
The vulnerability, which affected all GamiPress versions up to 7.3.1, was finally patched in version 7.3.2, released on March 18, 2025.
GamiPress Plugin: Unauthenticated SQL Injection FlawDuring an offsite security assessment, security researcher Abrahack identified the vulnerability while examining GamiPress plugin version 7.2.1.
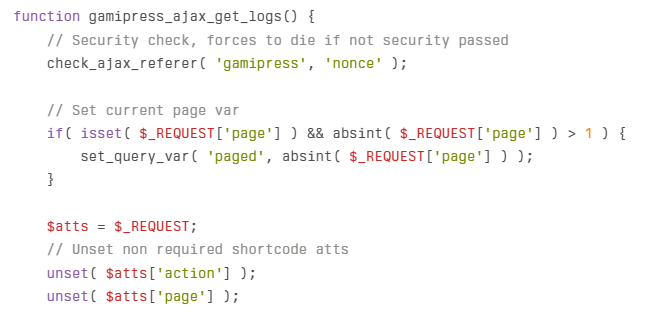
The vulnerability stemmed from improper input validation in the plugin’s log retrieval functionality, specifically in the gamipress_get_logs AJAX endpoint, which allows unauthenticated access through the WordPress hook wp_ajax_nopriv_{$action}.
This type of SQL injection vulnerability is hazardous because it requires no authentication to exploit. An attacker could potentially extract sensitive information from the database or even take control of the website.
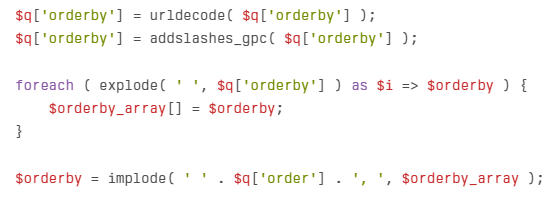
The plugin’s vulnerability existed in handling the orderby parameter in database queries. The vulnerable code in the plugin can be seen here:
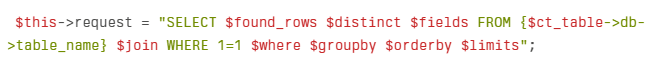
While the code attempted to sanitize inputs using sanitize_text_field(), the vulnerability occurred further down the execution chain in the CT_Query class, where the orderby parameter was unsafely incorporated into SQL queries:
The summary of the vulnerability is given below:
Risk Factors DetailsAffected Products GamiPress WordPress plugin, versions ≤ 7.2.1Impact SQL injection, Extracting sensitive information from the databaseExploit Prerequisites No authentication required; ability to send HTTP requests with manipulated ‘orderby’ parameterCVSS 3.1 Score 7.5 (High)
Patch Availability - The developers of GamiPress addressed the vulnerability by implementing a whitelist approach for the orderby parameter, restricting it to a predefined list of valid columns in the database table.
This approach effectively prevents attackers from injecting malicious SQL commands. Cybersecurity experts strongly urge WordPress website administrators using the GamiPress plugin to update to version 7.3.2 or later immediately. Additionally, administrators should:
Review server logs for any unusual activityImplement web application firewalls for additional protectionFollow security best practices for WordPress installationsThis vulnerability reminds us of the importance of regular security audits and prompt patching of content management systems and their extensions to maintain website security integrity.